I’m aware that most Monero users are tech-savvy and it is not easy to trick them with scams and phishing like this. So this article is only informational and precautionary.
On May 18, 2025, I received a spam email with the following subject: “Monero Interface Update: Desktop Enhancements, CLI Improvements, and Browser-Based Access”.
The Email
This caught my attention because email is a communication medium that is rarely used by the Monero community. I opened the email and it contained information about a major update and several improvements for the Monero GUI wallet. They also introduced a browser extension for the Monero Wallet. At the very bottom of the email, it said the email came from the “Monero Development Team” which is unreasonable.
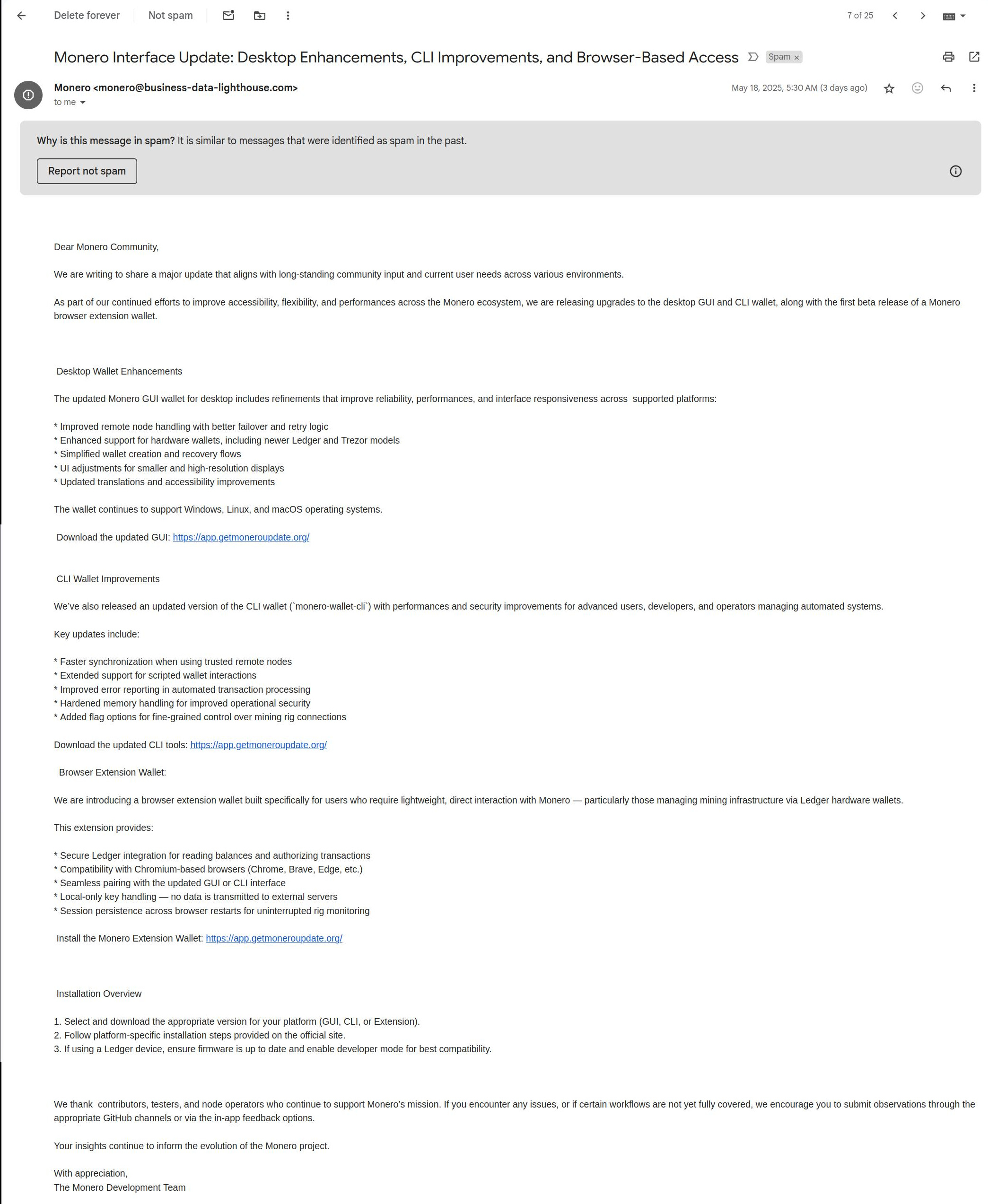
Why do I call it unreasonable? Because I believe that the Monero Core Team never sends updates to Monero users via email. The Core Team write an update overview every release in their GitHub repository, then the Monero community such as reuvo-xmr, monero.observer, Monero Talk, etc. helps spread the news through their respective media.
From here, I decided to dig up more information. The email was sent via the
monero [at] business-data-lighthouse [dot] com using the Amazon SES
service. Although SPF, DKIM and DMARC records status is “passed”, the email is
clearly not from getmonero.org.
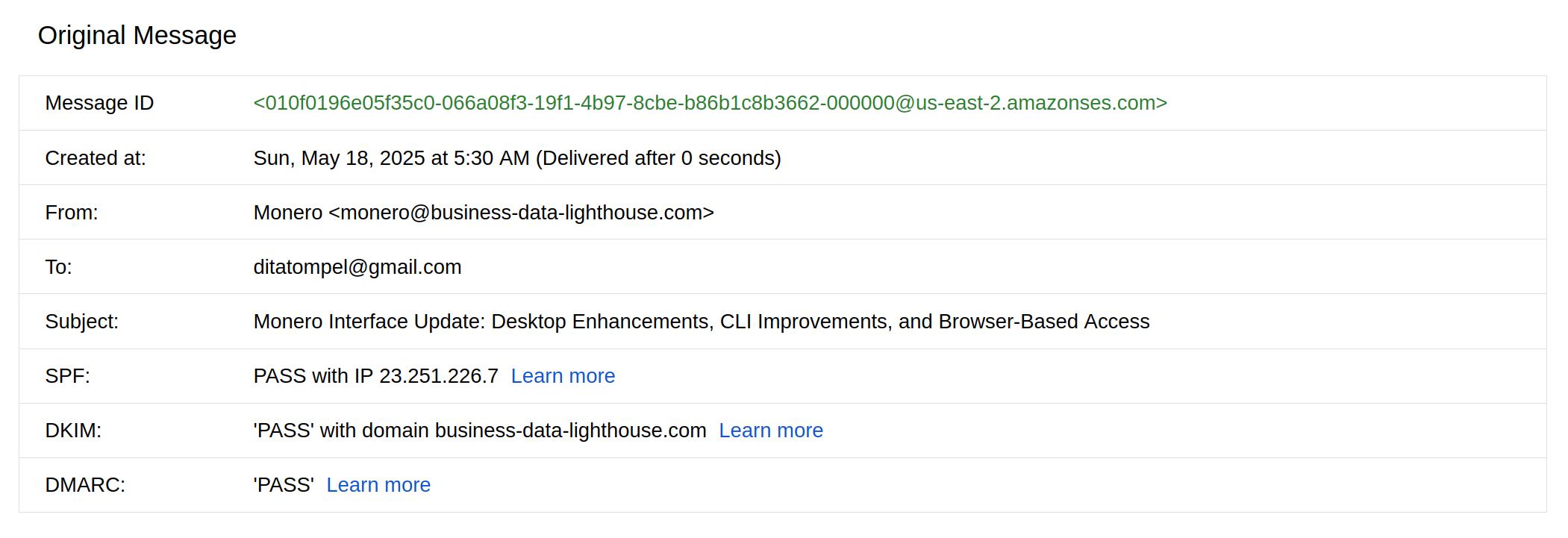
And it worth to mention that none of the sender domain name and Amazon SES
services are listed in getmonero.org SPF record.
Output of drill getmonero.org TXT -t | grep spf:
1getmonero.org. 284 IN TXT "v=spf1 mx ptr a:mail.getmonero.org ip4:74.220.215.227 ip4:74.220.200.165 include:_spf.google.com ~all"
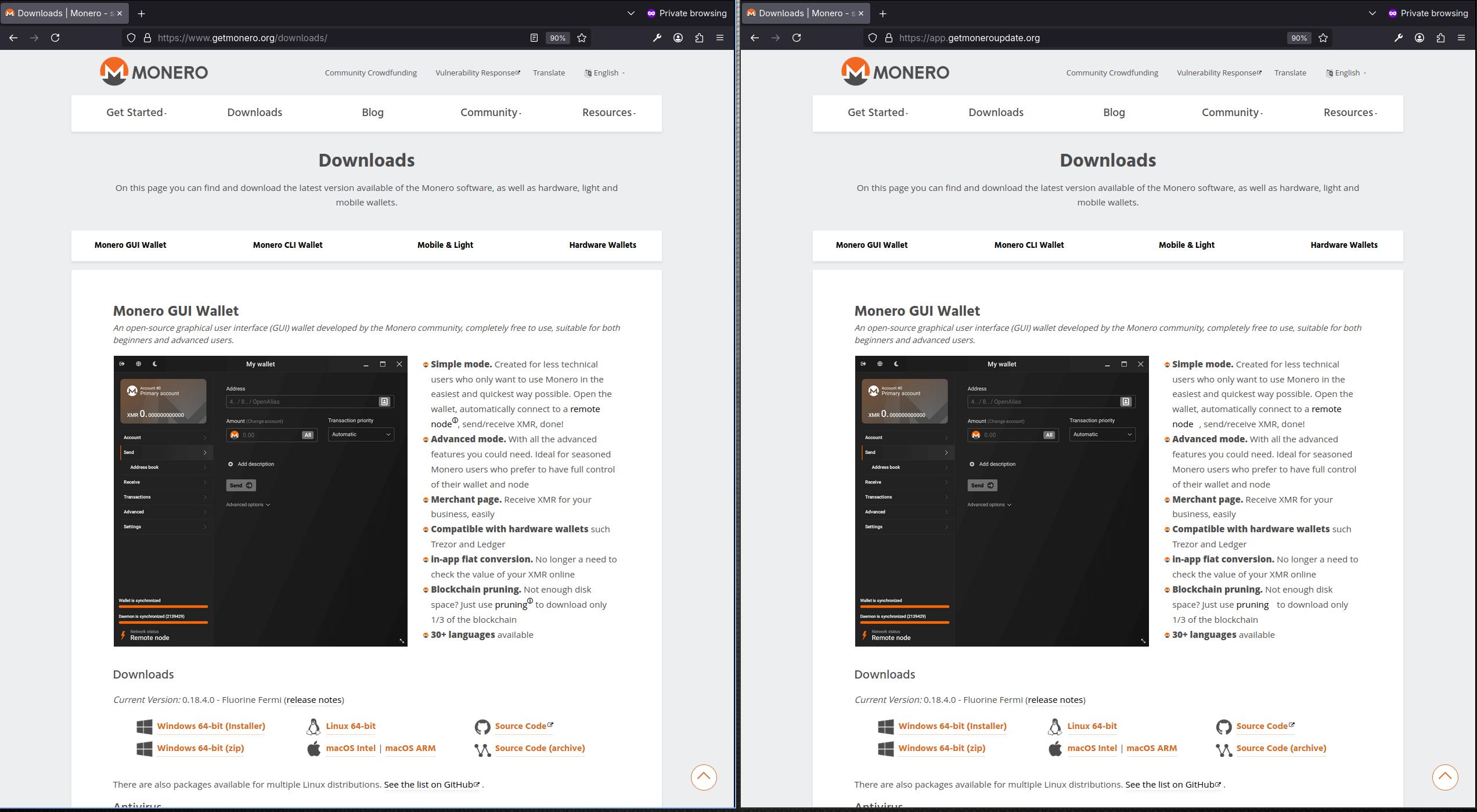
The Phishing Site
I decided to visit the download link listed in the email. The link leads to the
sub-domain app [dot] getmoneroupdate [dot] org which looks almost exactly the
same as the download page on getmonero.org. The only
difference is in the download link for each operating system and CPU
architecture.
Install on VM
I didn’t find the promised browser extension download link in the email, but
the .exe file, MacOS and Debian packages pointed to amandinetv [dot] com
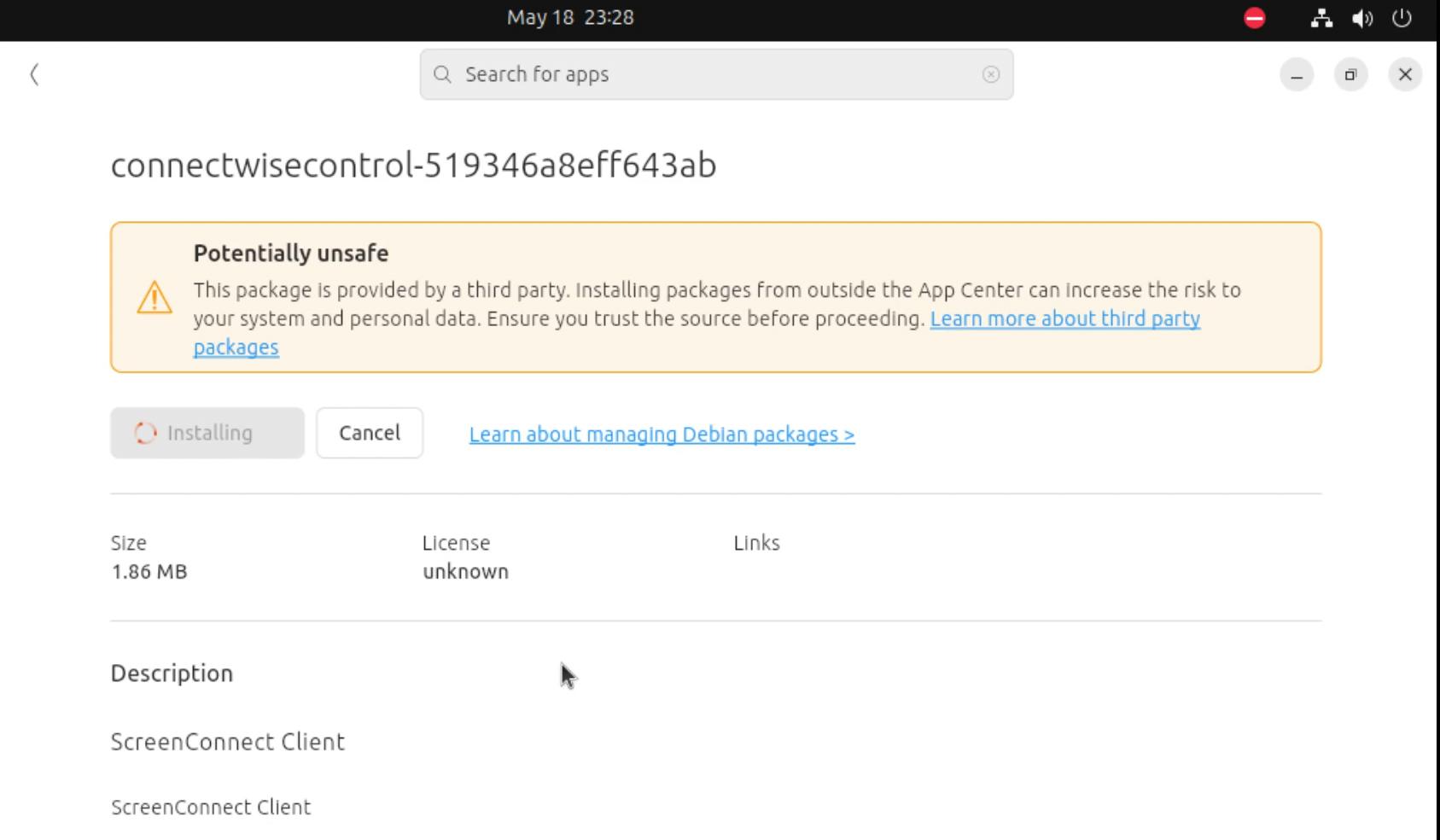
domain. Curious about what the “malware” was like, I decided to running the
.deb package on an Ubuntu virtual machine. I couldn’t install it with the
dpkg -i command due to dependency problem, but it seemed like the package
could be installed using the App Center (by double click on it).
Process, Init Script and tcpdump
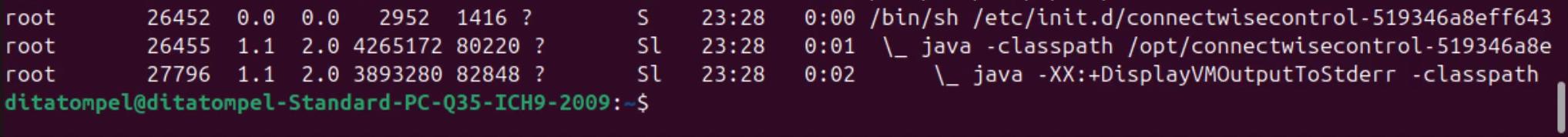
After the application was installed, I tried to find information about whether
the application was opening a port, but I didn’t find it either on TCP or UDP.
But from the ps command, it was seen that a Java program called
connectwisecontrol was running.
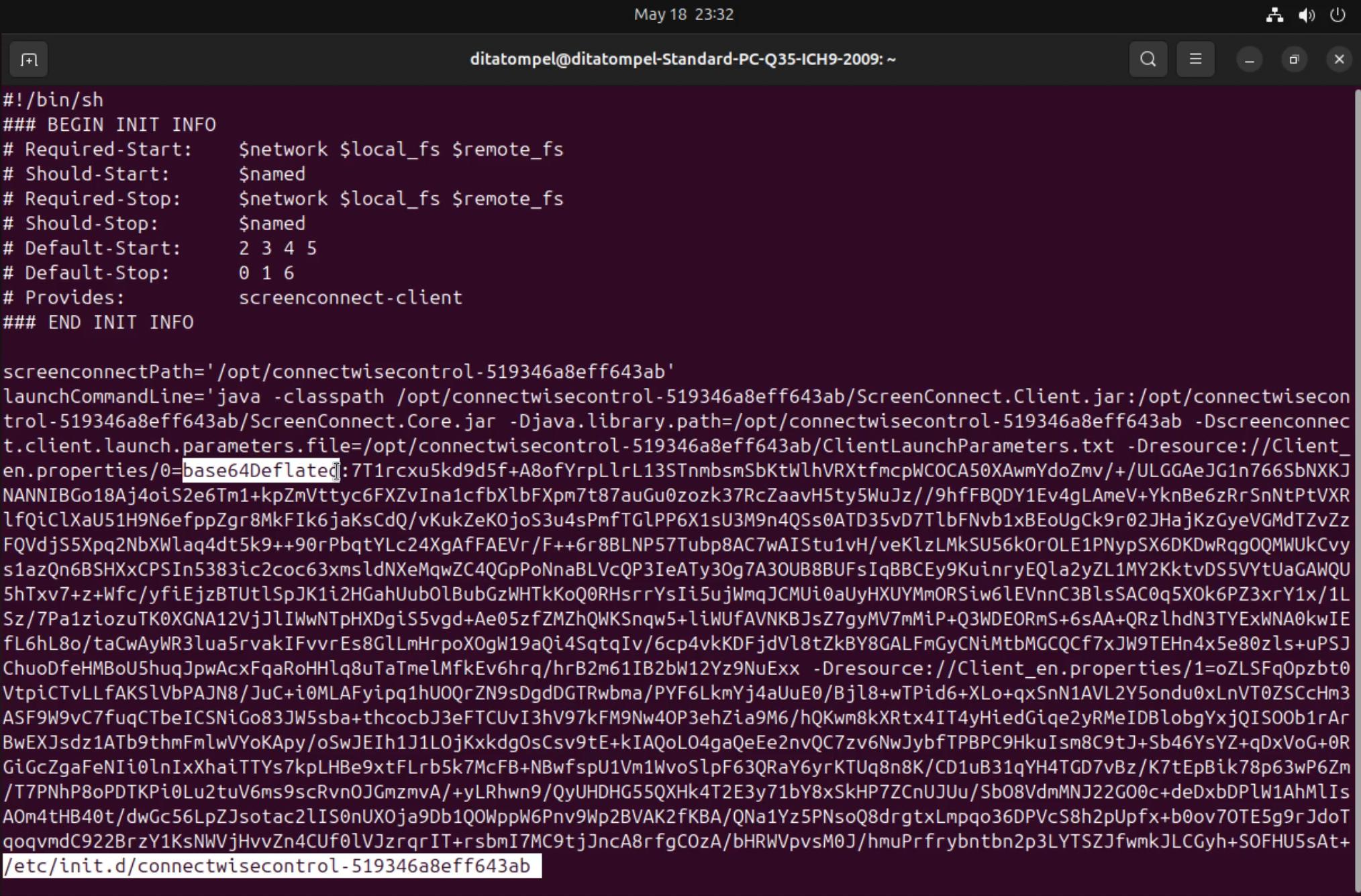
I tried to see the init script used to run the process and found several
command parameters and properties in the form of inflated base64.
tcpdump instead to find
information about where the process was communicating. The result of tcpdump
shows that the process is communicating to the control server (PTR record
23-95-162-71-host.colocrossing.com) on port 8041.
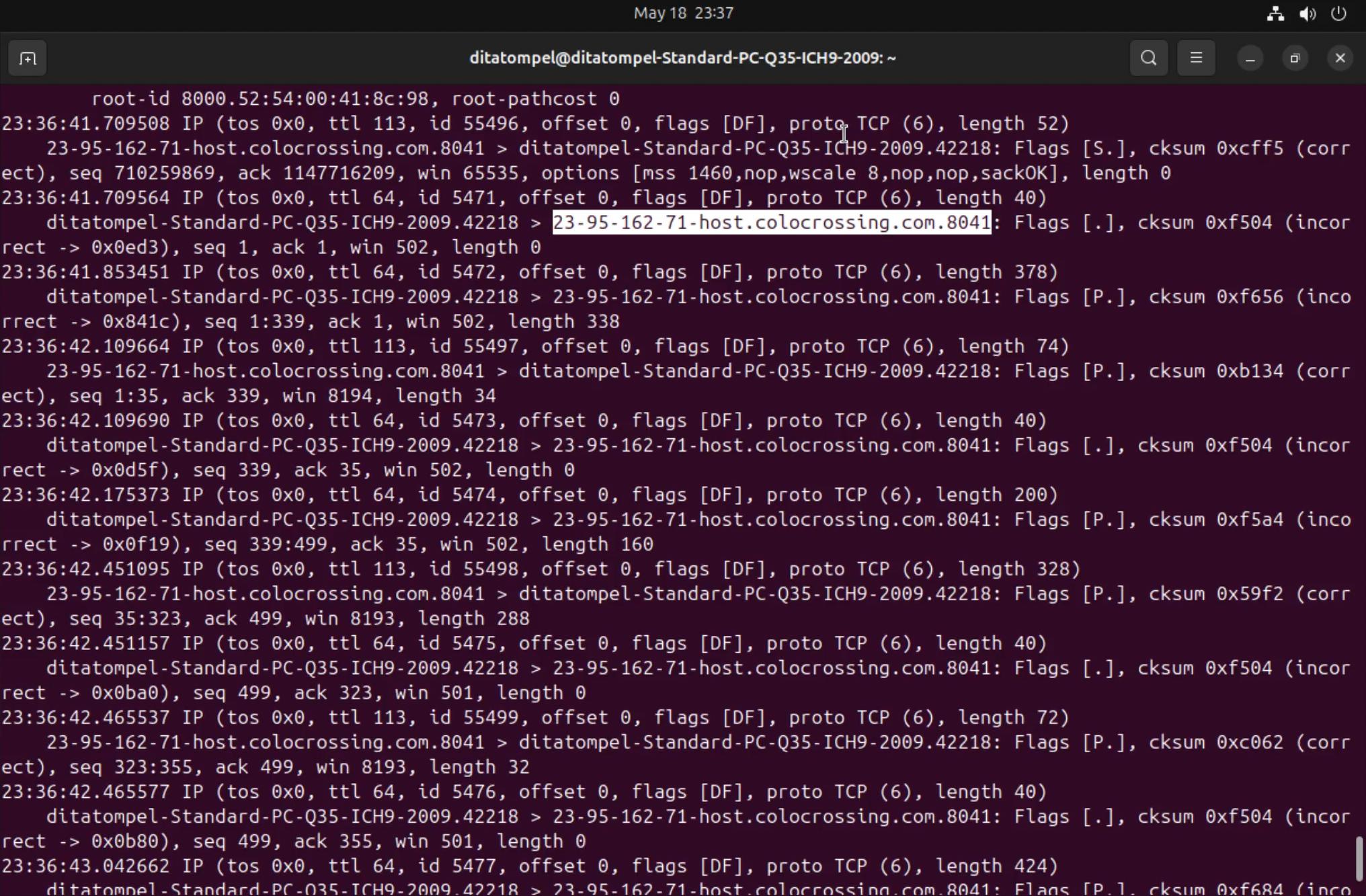
I searched for information about the connectwise application and found that ConnectWise Control is a remote desktop application that allows users to control and access target PCs via the internet. I personally never used ConnectWise Control (in fact, this is my first time I hear about it), but if it is something like RustDesk or AnyDesk, it is likely that the victims computer can be taken over by an attacker by utilizing the application.