A few days ago, I tried to “talk” with ChatGPT by OpenAI, discussing many things from the cost of cloud computing to quantum computer. I’m impressed with the ability to translate human language despite of my messy grammar and typos during conversation.
I record the conversation and upload it to my YouTube archive:
Summary
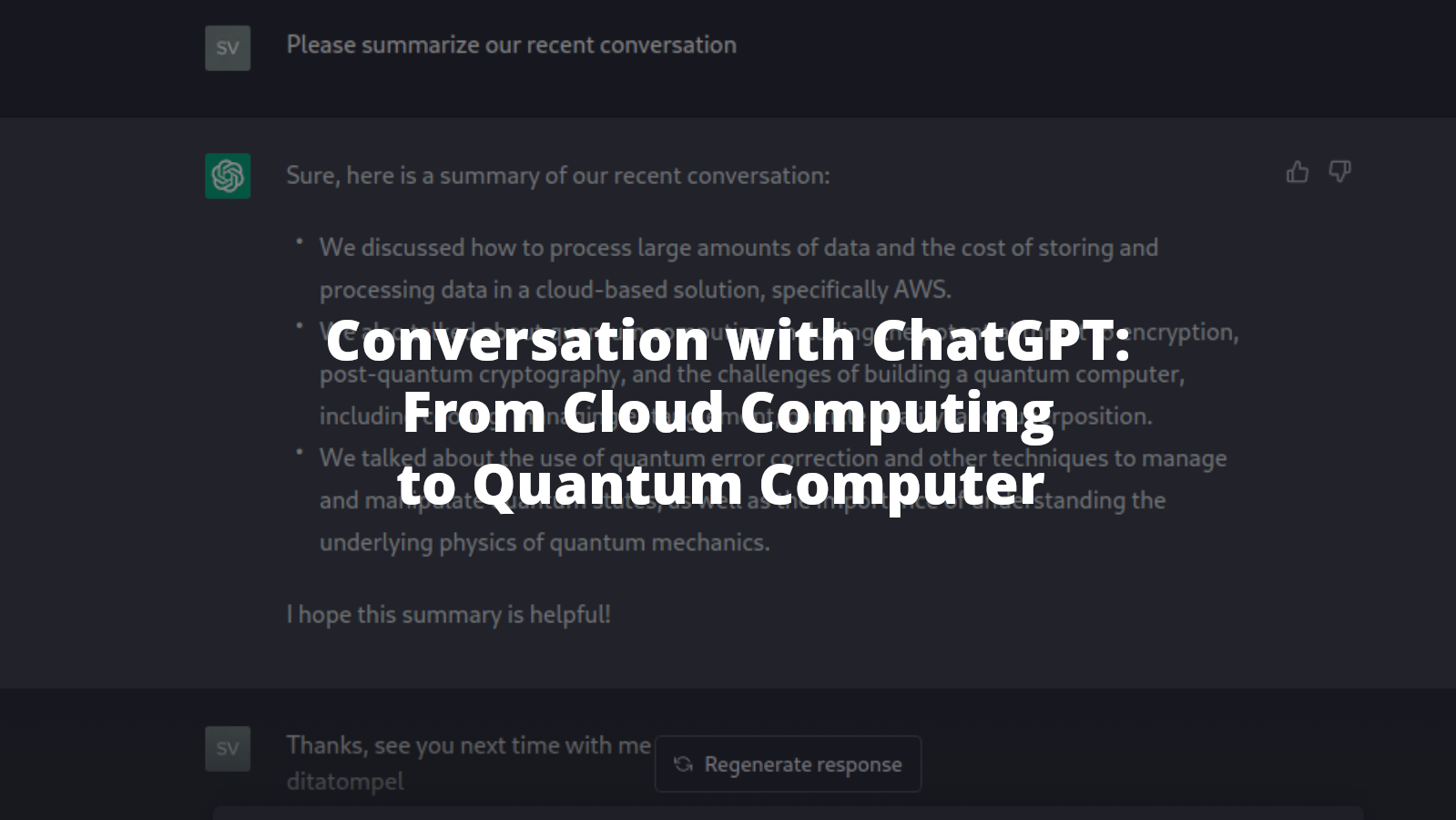
At the end of the conversation, I ask ChatGPT to summarizes our conversation and this is what I got:
- We discussed how to process large amounts of data and the cost of storing and processing data in a cloud-based solution, specifically AWS.
- We also talked about quantum computing, including the potential threat to encryption, post-quantum cryptography, and the challenges of building a quantum computer, including cooling, managing entanglement, particle duality, and superposition.
- We talked about the use of quantum error correction and other techniques to manage and manipulate quantum states, as well as the importance of understanding the underlying physics of quantum mechanics.
Transcript
Cloud Services
Q: I had hundreds of billions of data to process. About 200TB of data and still growing. How can I process that huge set of informations?
Processing hundreds of billions of data points, especially when the data set is 200TB or larger, can be a daunting task. Here are some tips to help you with this:
- Determine what kind of processing you need: Depending on what you want to do with the data, you may need to use different processing techniques. For example, if you need to run complex queries on the data, you may want to consider using a distributed computing system like Hadoop or Spark. If you need to analyze the data using machine learning algorithms, you may want to use a specialized machine learning platform like TensorFlow.
- Choose the right hardware: To process large data sets, you need hardware that can handle the load. You may want to consider using a high-performance computing system with multiple CPUs, GPUs, and large amounts of memory.
- Optimize your data processing: You can optimize your data processing by parallelizing your code, using data compression techniques, and using distributed file systems to store and access the data.
- Monitor the processing: With large data sets, processing can take a long time, and errors can be hard to spot. It is important to monitor the processing regularly to ensure it is running correctly and efficiently.
- Consider cloud-based solutions: Cloud-based solutions like Amazon Web Services (AWS) or Microsoft Azure can provide the infrastructure and tools needed to process large data sets efficiently and cost-effectively.
Keep in mind that processing large data sets is a complex and resource-intensive task, so you may want to consult with data processing experts to help you design and implement an efficient and scalable solution.
Q: I’m interested with cloud-based solutions. How much does it cost to store 200TB of data to datalake and process it with hundreds of millions of data set?
The cost of storing 200TB of data and processing hundreds of millions of data points in the cloud will depend on a number of factors, including the cloud provider, the type of storage and processing services you choose, the amount of data transfer involved, and the level of usage you require.
For example, if you use Amazon Web Services (AWS), the cost of storing 200TB of data in Amazon S3 (Simple Storage Service) will be approximately $2,850 per month at the current pricing as of February 2023. However, if you use a different storage service, such as Amazon Elastic File System (EFS) or Amazon Elastic Block Store (EBS), the cost will be different.
The cost of processing the data will also depend on the specific processing services you use, such as Amazon EMR (Elastic MapReduce), AWS Glue, or AWS Athena. The cost of these services can range from a few cents per hour to several dollars per hour, depending on the processing power and the level of usage.
In addition to the storage and processing costs, you will also need to consider the cost of data transfer, which can vary depending on the amount of data being transferred, the distance between the cloud provider and the source of the data, and the type of data transfer protocol being used.
Overall, the cost of storing and processing 200TB of data with hundreds of millions of data points in the cloud can be significant, and it is important to carefully evaluate the costs and benefits of different cloud-based solutions before making a decision.
Q: I was once use some of their services, and billed almost $2,500 in just 2 days!
Cloud service costs can vary widely depending on the specific services you use, the amount of usage you require, and other factors such as data transfer and storage costs. It’s important to carefully monitor your usage and keep track of costs to avoid unexpected bills.
Here are some tips to help you control your cloud service costs:
- Monitor your usage: Cloud providers typically provide detailed usage reports that show you how much you are using each service and how much it is costing you. Regularly monitoring your usage can help you identify areas where you may be able to optimize or reduce your usage.
- Use cost-effective services: Cloud providers offer a range of services with different pricing structures. Choosing the right service for your needs can help you keep costs down. For example, using reserved instances or spot instances can be more cost-effective than using on-demand instances for some workloads.
- Optimize your infrastructure: Carefully designing your infrastructure to optimize for cost and efficiency can help you avoid unnecessary spending. This may include using autoscaling to adjust capacity based on demand, using smaller instances where possible, and leveraging cloud provider tools for cost optimization.
- Use cost management tools: Cloud providers offer tools and services to help you manage and optimize your costs. For example, AWS provides the AWS Cost Explorer, which allows you to analyze your spending, identify cost drivers, and forecast your costs.
- Set spending limits: Most cloud providers allow you to set spending limits to prevent unexpected bills. You can set alerts and automate actions based on your spending, such as stopping services or scaling down capacity.
By following these tips, you can better control your cloud service costs and avoid unexpected bills.
Q: The cost management / monitoring tools is just an alert if your bill near your billing threshold. It doesn’t automatically stop the services.
You are correct that many cost management and monitoring tools provided by cloud service providers will alert you when your spending approaches a threshold that you set, but may not automatically stop your services. However, some cloud providers, such as AWS, do provide tools that allow you to automate actions based on your spending.
For example, AWS Budgets allows you to set a spending limit and configure an alert when your spending reaches a certain percentage of your budget. You can also set up an automatic action, such as stopping an instance or terminating a service, when your spending reaches a certain threshold.
Similarly, AWS Trusted Advisor provides recommendations for optimizing your costs and improving your infrastructure based on your usage patterns. Trusted Advisor can also alert you to potential cost savings opportunities and provide guidance on how to optimize your resources.
In addition, there are third-party cost management tools available that can provide more advanced cost management and automation features, such as automated scaling based on cost, detailed cost analytics, and custom dashboards.
Ultimately, the key to effective cost management in the cloud is to closely monitor your usage, regularly review your infrastructure, and use the tools and services available to optimize your resources and control your costs.
Quantum Computing
Q: Thanks for the info about AWS budget. Let’s talk about another topic. Do you know about quantum computer?
Yes, I am familiar with quantum computers. Quantum computers are a new type of computer that use the principles of quantum mechanics to process information. Unlike classical computers, which use bits that can be either 0 or 1, quantum computers use qubits, which can be in a superposition of states, allowing them to represent multiple values at once. This makes quantum computers potentially much faster than classical computers for certain types of problems.
One of the most promising applications for quantum computers is in the field of cryptography, where they could be used to break many commonly used encryption algorithms. However, quantum computers are still in the early stages of development, and many technical and practical challenges need to be overcome before they become widely used.
There are several organizations and companies, including IBM, Google, and Microsoft, that are actively working on developing quantum computers and exploring their potential applications. Some of the key technical challenges in building a practical quantum computer include developing stable qubits, reducing errors, and scaling up the system to handle larger problems.
Q: Is quantum computer is real thread to encryptions?
Yes, quantum computers have the potential to be a significant threat to many commonly used encryption algorithms, especially those based on the factoring of large numbers or computing discrete logarithms. These algorithms, which are used in many public key encryption schemes, are vulnerable to attacks using Shor’s algorithm, a quantum algorithm that can efficiently factor large numbers and solve certain types of discrete logarithm problems.
If a large enough quantum computer is developed, it could be used to break many commonly used encryption algorithms, potentially exposing sensitive information and causing significant disruptions to industries that rely on secure communication and data storage.
To address this threat, researchers are working on developing new post-quantum cryptography schemes that are resistant to quantum attacks. These schemes are designed to be secure even against attacks using quantum computers, making them a promising alternative to traditional encryption algorithms.
Q: Tell me about post-quantum cryptography Post-quantum cryptography (also known as quantum-resistant cryptography) is a type of cryptographic algorithm that is designed to be secure against attacks by both classical and quantum computers. Post-quantum cryptography is becoming increasingly important due to the potential threat that quantum computers pose to many commonly used encryption algorithms.
The most widely studied and promising approach to post-quantum cryptography is lattice-based cryptography. Lattice-based cryptography is based on the hardness of certain mathematical problems related to lattices, which are geometric structures in higher-dimensional space. These problems are believed to be resistant to attacks by both classical and quantum computers, making lattice-based cryptography a promising candidate for post-quantum cryptography.
Other approaches to post-quantum cryptography include code-based cryptography, hash-based cryptography, and multivariate cryptography. Each of these approaches has its own strengths and weaknesses, and researchers are continuing to explore their potential for providing secure encryption in a post-quantum world.
As the development of quantum computers continues, it’s becoming increasingly important for organizations to start preparing for the post-quantum era by evaluating their current cryptographic systems and developing a plan for transitioning to post-quantum cryptography. This may involve implementing new post-quantum cryptographic algorithms, or using a hybrid approach that combines classical and post-quantum cryptography to provide additional security.
Q: What is the biggest challenge in building quantum computer?
There are several major technical and practical challenges in building a practical quantum computer. Some of the biggest challenges include:
- Developing stable qubits: Quantum computers rely on qubits, which are much more fragile than classical bits. Qubits are susceptible to decoherence, which is the loss of quantum coherence due to interaction with the environment. Maintaining qubits in a coherent state for long enough to perform meaningful calculations is a major technical challenge in building quantum computers.
- Reducing errors: Quantum computers are also susceptible to errors due to decoherence, as well as errors in hardware and software. Reducing errors is crucial for building a practical quantum computer that can perform meaningful calculations.
- Scaling up the system: Currently, quantum computers are limited in their ability to perform meaningful calculations due to the small number of qubits that can be reliably used. Scaling up the system to handle larger problems requires not only developing more qubits, but also building reliable systems to control and read out the qubits.
- Developing new algorithms: While quantum computers can potentially solve certain types of problems much faster than classical computers, developing new algorithms that can take advantage of this speedup is a significant challenge. Many existing algorithms that are used in classical computing may not be well-suited for quantum computers.
- Overcoming practical challenges: In addition to these technical challenges, there are also many practical challenges involved in building a practical quantum computer, such as developing reliable and efficient cooling systems, managing the vast amounts of data that quantum computers can generate, and ensuring that quantum computers are safe and secure to use.
Despite these challenges, significant progress has been made in the development of quantum computers in recent years, and many experts believe that quantum computers will eventually become a practical tool for solving some of the world’s most challenging problems.
Q: You mention about the “efficient cooling systems”. Is it true that quantum computer need isolated environment with very low temperature (near absolute-zero)?
Yes, it is true that quantum computers require an isolated environment with very low temperatures in order to operate. This is because quantum computing relies on the manipulation of quantum states, which are extremely sensitive to interference from their environment. Even the slightest interaction with the environment can cause decoherence and destroy the delicate quantum states that are being used to perform calculations.
To avoid this, quantum computers must be shielded from external electromagnetic fields, vibrations, and temperature fluctuations. They are typically housed in specialized facilities called quantum labs, which are designed to provide an isolated and highly controlled environment.
One of the key requirements for this environment is a very low temperature, typically around 10 to 20 millikelvin (0.01 to 0.02 Kelvin), which is just a fraction of a degree above absolute zero. This is because at such low temperatures, the thermal energy of the surrounding environment is minimized, which reduces the likelihood of decoherence.
To achieve such low temperatures, quantum computers use specialized cooling systems, such as dilution refrigerators or adiabatic demagnetization refrigerators, which can cool the qubits to near absolute zero temperatures. These cooling systems are highly complex and expensive, and require a significant amount of energy to operate.
Overall, providing a highly controlled and isolated environment for quantum computers is one of the key technical challenges in developing practical quantum computing systems.
Q: External electromagnetic fields? Did you mean cosmic rays that can cause bit-flip?
Yes, cosmic rays are one example of an external electromagnetic field that can interfere with the operation of a quantum computer. Cosmic rays are high-energy particles that are constantly bombarding the Earth’s atmosphere, and they can cause ionization and other effects that can lead to errors in qubits.
In addition to cosmic rays, there are many other sources of electromagnetic interference that can affect the operation of a quantum computer. For example, even the electrical current used to power the computer can create electromagnetic fields that interfere with the delicate quantum states being used to perform calculations.
To avoid this interference, quantum computers must be carefully shielded and isolated from their environment. This typically involves using specialized materials that block electromagnetic radiation, as well as physical isolation from sources of interference, such as other electronic devices or even people.
In addition to shielding and isolation, quantum computers also use error correction techniques to mitigate the effects of electromagnetic interference and other sources of noise. These techniques involve redundantly encoding quantum information to detect and correct errors, and they are an active area of research in the field of quantum computing.
Q: Is ECC memory is not good enough to deal with cosmic rays?
ECC (Error-Correcting Code) memory can detect and correct single-bit errors in memory, which can be caused by various factors including cosmic rays. However, ECC memory is not designed to deal with multi-bit errors, which are more common in quantum computers due to their high sensitivity to external noise.
Quantum computers require much stronger error correction techniques than traditional computers, because the quantum states used to perform computations are extremely delicate and can easily be disrupted by even the slightest bit of noise or interference. To address this, quantum error correction techniques have been developed that can detect and correct multi-bit errors, as well as other types of noise that are specific to quantum systems.
Quantum error correction is an active area of research, and a number of different techniques have been proposed. These techniques generally involve encoding quantum information across multiple qubits, and then performing operations on these qubits to detect and correct errors.
Overall, while ECC memory can provide some protection against cosmic rays and other types of external interference, it is not sufficient for the much more complex error correction requirements of quantum computing.
Q:Tell me, how those who develop quantum computer deals with quantum entanglement and particle duality?
Quantum entanglement and particle duality are fundamental features of quantum mechanics, and they play a critical role in the design and operation of quantum computers.
Quantum entanglement is a phenomenon in which two or more quantum particles become correlated in such a way that the state of one particle depends on the state of the others, even if they are physically separated. Entanglement is a powerful resource for quantum computing, as it allows qubits to be used in ways that are not possible in classical computing. However, it also presents challenges for quantum computing, as it requires careful management to prevent unwanted interactions between entangled qubits.
Particle duality, on the other hand, is the idea that quantum particles can exist as both waves and particles, and that their behavior is determined by the act of measurement. This has important implications for quantum computing, as it means that the act of measuring a qubit can change its state, potentially introducing errors into computations.
To address these challenges, quantum computing researchers and engineers use a variety of techniques and technologies. One of the most important is quantum error correction, which is used to detect and correct errors in quantum states, including those caused by entanglement and particle duality.
Other techniques used to manage entanglement and particle duality include the use of decoherence-free subspaces, which allow qubits to be protected from environmental noise and other sources of interference, and the use of entanglement purification techniques, which allow unwanted entanglement between qubits to be removed.
In addition, many quantum computing systems are designed to carefully manage the interactions between qubits, in order to prevent unwanted entanglement and other sources of noise. This can involve the use of physical isolation and shielding, as well as the use of specialized control systems that can precisely manipulate the states of individual qubits. Overall, managing entanglement and particle duality is a key challenge in developing practical quantum computing systems, and requires a deep understanding of the underlying physics of quantum mechanics.
Q: How about the superposition state?
Superposition is another fundamental feature of quantum mechanics that plays a critical role in quantum computing. In quantum mechanics, particles can exist in a superposition of multiple states simultaneously, rather than being confined to a single state as in classical physics.
In the context of quantum computing, superposition is used to encode information in quantum states. In a classical computer, a bit can be either 0 or 1, but in a quantum computer, a qubit can exist in a superposition of both 0 and 1 states at the same time. This allows quantum computers to perform certain computations much more efficiently than classical computers.
However, managing and manipulating superposition is a major challenge in quantum computing. The superposition state is extremely fragile, and can be easily disrupted by even tiny amounts of external noise or interference. This can lead to errors in computations, and is one of the main reasons why building a practical quantum computer is so difficult.
To address this challenge, quantum computing researchers use a variety of techniques to carefully control and manipulate the states of qubits. This can involve using specialized hardware to create and manipulate superposition, as well as using specialized control systems to protect qubits from environmental noise and other sources of interference.
In addition, quantum error correction techniques can be used to detect and correct errors in quantum states, including those caused by unwanted interactions with the environment. Overall, managing and manipulating superposition is a critical challenge in quantum computing, and requires a deep understanding of the underlying physics of quantum mechanics.
Q: Please summarize our recent conversation Sure, here is a summary of our recent conversation:
- We discussed how to process large amounts of data and the cost of storing and processing data in a cloud-based solution, specifically AWS.
- We also talked about quantum computing, including the potential threat to encryption, post-quantum cryptography, and the challenges of building a quantum computer, including cooling, managing entanglement, particle duality, and superposition.
- We talked about the use of quantum error correction and other techniques to manage and manipulate quantum states, as well as the importance of understanding the underlying physics of quantum mechanics.
I hope this summary is helpful!
Thanks, see you next time with me again.
ditatompel
You’re welcome! Feel free to reach out to me anytime you have questions or want to chat. Have a great day!