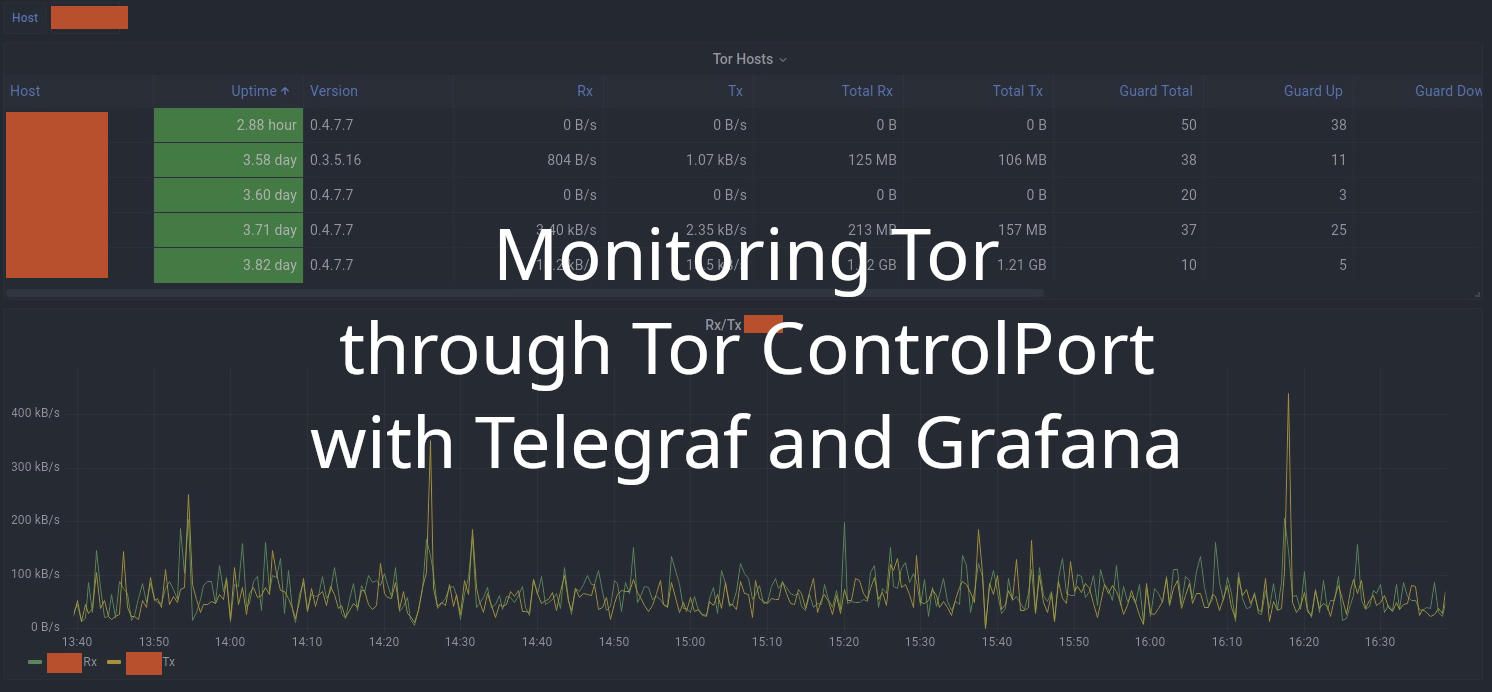
Sometime, I get a problem when running Tor daemon under Linux Container, usually related to AppArmor after I upgrade the system. Meanwhile, my Tor service needs to be turned on all the time and reachable to all my “workers” who fetch .onion addresses listed on my Monero remote node monitoring service.
Lucky for me, a few days ago I found a python script written by bentasker. The script takes data from Tor ControlPort and converts it to InfluxDB format (it also support relay / exit node metrics if you run one, cool isn’t it?). It’s very easy to set up, just download tor-daemon.py and follow the instructions given on that page and you’re done.
TLDR
- Generate password hash using
tor --hash-password <your_secret_password>. - Copy generated hash, enable Tor
ControlPortand add (or replace)HashedControlPasswordto your generated hash (don’t forget to restart Tor service after you changetorrcconfig). - Download tor-daemon.py script and place it somewhere, edit
CONTROL_H,CONTROL_P, andAUTHvariable so it fit with your configured TorControlPortsettings. - Add Telegraf
input.execconfiguration to trigger the script.
Please read detailed information about how to configure and monitoring the Tor daemon with Telegraf on Ben’s website (and I’m sure you’ll love reading all the posts on his website, like I do).