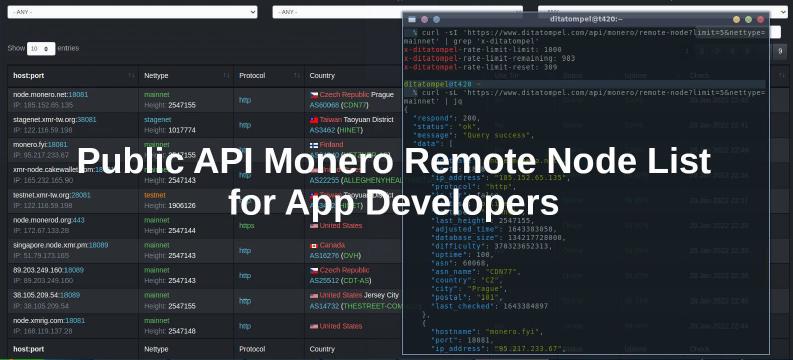
ditatompel Insights
Plex discovered that a third-party was able to access a limited subset of their user data that includes emails, usernames, and encrypted passwords
ditatompel Insights
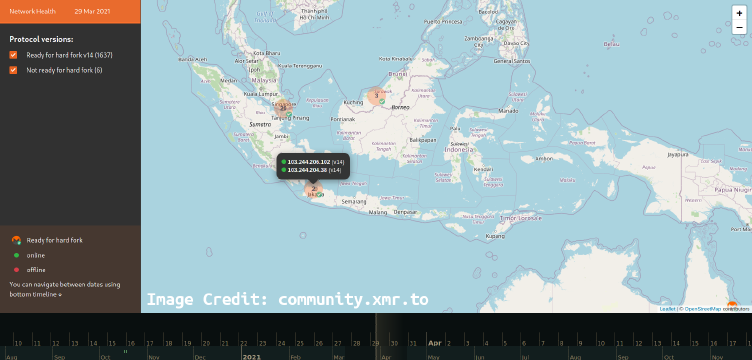
The origin of Monero (timeline, notable event, moment and incident). Note: This article is not done yet, working on progress